Aembit, a Maryland-based security startup that focuses on helping DevOps and security teams manage how federated workloads talk to each other, is officially launching its service today and announcing a $16.6 million seed funding round from Ballistic Ventures and Ten Eleven Ventures.
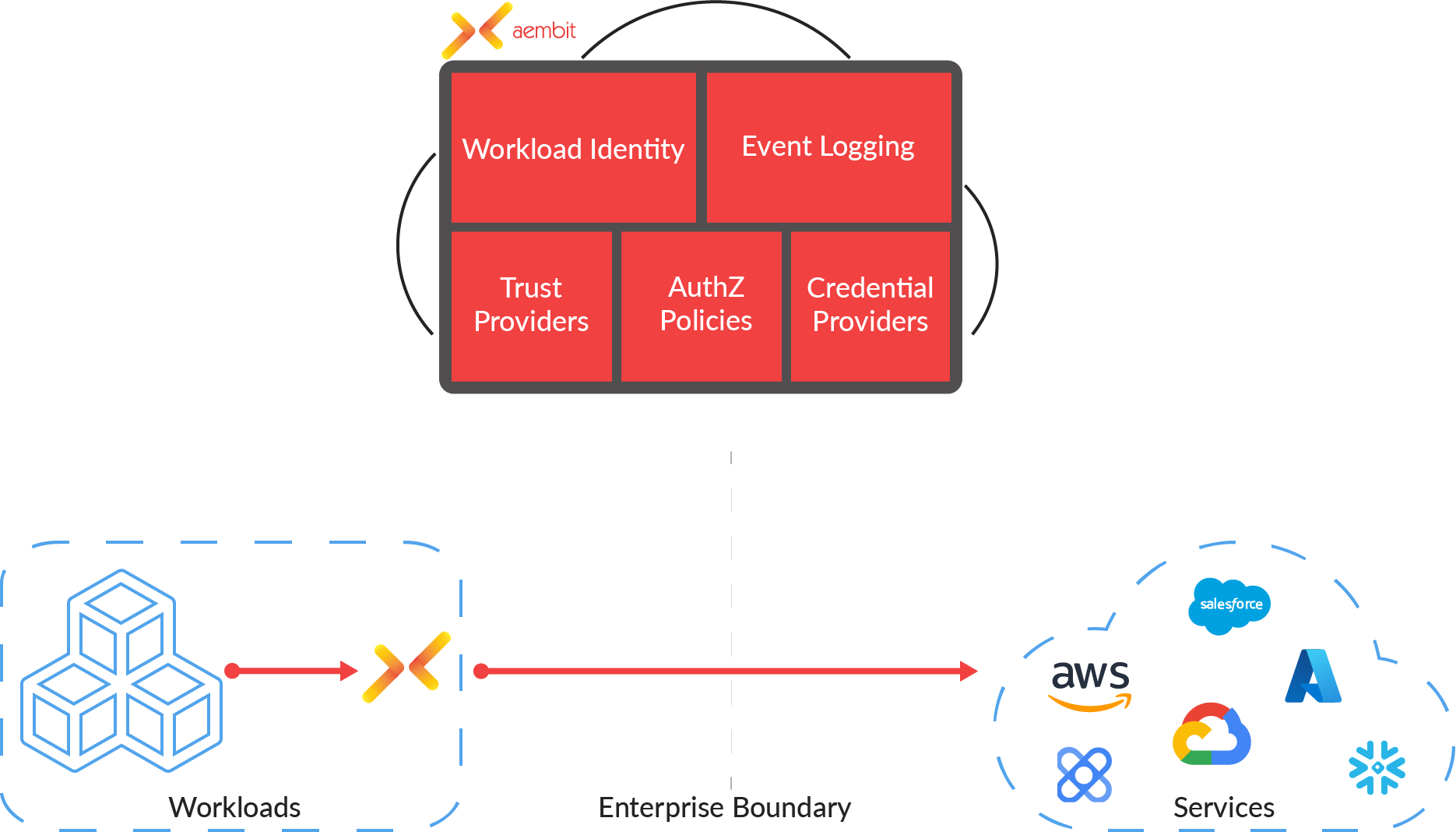
In essence, Aembit’s workload identity and access management service applies industry knowledge, from managing user and device access to cloud workloads such as APIs, databases and other cloud resources — all without requiring developers to make changes to their code.
The co-founders, David Goldschlag and Kevin Sapp, spent the last 17 years working together. Among other startups, they co-founded the zero trust platform New Edge Labs, which was acquired by Netskope, and the mobile device management platform Trust Digital, which was acquired by McAfee.
“Along the way, people would always ask us: what about workload-to-workload application-level access? It’s always been this thing that’s there and that’s important, but we hadn’t addressed it,” Goldschlag explained. When the founders left Netskope in the summer of 2021, they decided to finally tackle this challenge. “It was important, because you had all these things happening in the ecosystem, right? You had all of these APIs that were becoming part of people’s applications,” he noted. “If you think about open source from a couple of years ago, people built apps by including open source. Today, people build apps by including databases and APIs — and now you need to enable secure access between those.”
He noted that Aembit’s mission is different from that of API gateways and security services. These services live in front of the API and help developers build and expose those securely to internal and third-party developers. But Aembit’s focus is on the client that accesses the API and ensures that this client is authorized to access it. He likened it to how today’s identity management systems help enterprises authorize their users. When a user uses Okta to log into Microsoft 365, for example, that user interacts with Okta and then gets the credential to access the service.
To do all of this, Aembit also has to become the system of record not just for all of these workload identities but also the workloads themselves (and these days, those workloads are often ephemeral, making this an even harder problem).
“You want to start with the foundational level, which is you have identities and you have policies. You enable access and you log this. But you probably want to discover more and more workloads from all these fragmented places — and then you may want to discover access patterns,” Goldschlag explained. “Our system can already do that. We can deploy the system in a non-enforcement mode — a discovery mode — to tell us what accesses are happening.”
Then, using this as a roadmap, it becomes much easier to see how these workloads typically interact — and take action when something changes.
“Enterprises have spent significant resources securing the connections between people and the software they use. However, as businesses move to the cloud, a new and fast growing attack surface has emerged,” said Jake Seid, co-founder and general partner of Ballistic Ventures. “The mesh of workload-to-workload connections created when software talks to other software need to be identified, secured and managed. Aembit is defining this new category of Workload IAM to defend enterprises’ most critical digital assets. It’s been an honor to work with the Aembit founders since day 1 and to continue to support them on their journey.”
Aembit currently has 11 full-time employees, virtually all of them in engineering. With the new funding, the company plans to grow its marketing team and build out its product. Specifically, Aembit, which has been doing well in selling to large enterprises, plans to launch a self-serve product soon, which will allow it to expand to more small and medium-sized businesses, too.